



Russian threat actors are suspected to have leveraged and believed to have exploited a zero-day vulnerability CVE-2021-1879 in the wild leveraging LinkedIn messaging and sending spear-phishing emails with malicious links.
Based on our research and analysis, we suspect state-sponsored Russian threat actor – Cozy Bear to be carrying out these activities targeting multiple industries and geographies. These activities are suspected to be part of the data exfiltration campaign codenamed “Crop Up.”
The primary motive of this campaign appears to be the exfiltration of sensitive information, intellectual property, personal, customer, and financial information.
Russian threat actors are suspected to have leveraged malware/ransomware and are believed to have exploited a zero-day vulnerability CVE-2021-34527.
Based on our research and analysis, we suspect state-sponsored Russian threat actor – TA505 or its affiliates to be carrying out these activities targeting multiple industries and geographies. These activities are suspected to be part of a global ransomware campaign codenamed “Night Blood.”
CYFIRMA suspects potential collaboration between Chinese hackers and Russian cybercriminals based on the indicators observed and given that Chinese hackers have targeted Japanese organizations with the same malware exploit kits in the past.
The primary motive of this campaign appears to be the exfiltration of sensitive information, intellectual property, personal, customer, and financial information.
The following malware use phishing and social engineering techniques as their initial attack vector. Apart from these techniques, exploitation of vulnerabilities and defense evasion tactics were also observed.
Often called one of the most ruthless and unreliable ransomware gangs by researchers, the Conti ransomware has now completed more than a year of attacking organizations. Unlike other successful ransomware operators who are particular about their reputation, Conti is known to be unreliable after receiving the ransom. The ransomware group continues to remain the top ransomware, affecting multiple businesses in the past week.
The LemonDuck malware, over the years has been known for its cryptocurrency mining and botnet capabilities. The malware is evolving into a much broader threat, moving into new areas of cyberattacks, targeting both Linux and Microsoft systems, and expanding its geographical reach.
The Lockbit ransomware operations launched in September 2019 as a ransomware-as-a-service (RaaS). Over the years the ransomware has remained active with a representative promoting and providing support on underground forums. With the ban of ransomware underground forums, LockBit began promoting the new LockBit 2.0 on their data leak site. Among the long list of features of the new version, the most notable one as per researchers is that the LockBit 2.0 automates interaction and subsequently encrypts the Windows domain using Active Directory group policies
The XCSSET malware known for targeting the macOS operating system has been updated once again. The malware has added more features to its toolset allowing it to amass and exfiltrate sensitive data stored in a variety of apps. As part of refinements in its tactics, XCSSET is now seen targeting Google Chrome and Telegram.
Suspected Threat Actors: Kimsuki
Summary
Researchers disclose information on North Korean APT group Kimsuki activity. The group is known to target South Korean think tanks & government organizations and have expanded its target region to United States, Russia, as well as Europe. As per researchers, the primary motive of the group is to gather intelligence and espionage. Throughout the first half of 2021, the group has mainly targeted South Korean organizations.
Insights
In terms of infrastructure, Kimsuki is good at using third-party cloud disks, personal blogs, personal mailboxes, and compromised websites as transit servers or attacking infrastructure, and the group excels at using various scripts such as vbs, bat, and other attack chains. In recent years, new tools have been constantly updated and developed.
From the activity observed in the first half of 2021, researchers categorized the decoy documents into below five categories. Most documents were aimed at collecting information.
Summary
The new version of the LockBit 2.0 ransomware automates the encryption of a Windows domain using Active Directory group policies. After the ban of ransomware topics on underground forums, LockBit began promoting their new LockBit 2.0 RaaS operation on their data leak site. The new version of LockBit comes with numerous advanced features including the use of group policy update to encrypt the network. The developers claim to have automated the ransomware distribution throughout. Once gaining control of the domain controller, threat actors utilize third-party software to deploy scripts that disable antivirus and then execute ransomware infecting machines on the network.
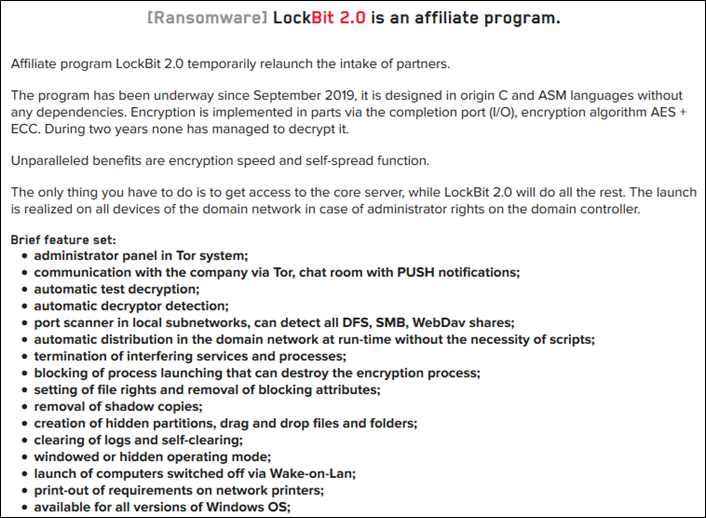
Source: Dark Web
Insights
A LockBit 2.0 ransomware sample analyzed by researchers confirms that threat actors have an automated process and distribute themselves throughout a domain when executed on a domain controller.
When executed, the ransomware creates new group policies on the domain controller that are then pushed out to every device on the network. These policies disable the Microsoft Defender’s real-time protection, alerts, submitting samples to Microsoft, default actions when detecting malicious files, and create a scheduled task. During the process, the ransomware also uses Windows Active Directory APIs to perform LDAP queries against the domain controller’s ADS to get a list of computers
The MountLocker ransomware group had previously used Windows Active Directory APIs to perform LDAP queries, however, this is the first time ransomware automated the distribution of the malware via group policies.
Summary
Disclosed earlier this week the zero-day flaw that exists in iOS and macOS platforms – being actively exploited in the wild – can allow attackers to take over an affected device. Tracked as CVE-2021-30807 is a memory-corruption vulnerability IOMobileFrameBuffer extension present in both iOS and macOS. In an event of successful Exploitation the vulnerability -2021-30807 can allow for attackers to execute arbitrary code with kernel privileges. Patches have been released for the vulnerability on each of the platforms and Apple is urging users to install the updates.
Insights
It should be noted that Apple has acknowledged the issue may have been actively exploited. Moreover, a researcher has separately published a POC.
As users update to fix yet another Apple zero-day vulnerability, they are also reportedly awaiting patches for flaws that make their devices easy prey for Pegasus spyware. Last week’s news reports suggest the notorious Pegasus mobile spyware from Israeli-based NSO Group is exploiting a zero-click zero-day in Apple’s iMessage feature.