



There is a very good chance that you are reading this article on your mobile device, with perhaps 1-2 other apps simultaneously open through which you are either shopping for daily groceries, killing zombies or checking your bank statement.
What started out as a device for voice communication has redefined wireless communication and connectivity through video calls, social media platforms, online shopping and has turned into a vibrant storehouse of precious professional as well as personal data. For cybercriminals, this playground of unsecured mobile devices is like a free ticket to Disneyland.
To understand why any device is under attack, one must first figure out what attackers are looking for. Cybercriminals, especially ransomware groups, are constantly looking for data that carry commercial value. This data – which if lost or sold – can bring in major repercussions like damage to personal reputation as well as significant financial loss.
Now, given that your mobile phones carries very personal and private data that is beyond just the contact details of your family and friends, it has emerged as one of the top attack surface vectors for several cyber-attacks.
It is not just the availability of critical personal information and financial data but also the fact that mobile security is still in a nascent stage which makes it a low-hanging fruit for cybercriminals. In 2021, the number of mobile devices stood at almost 15 billion and is expected to reach 18.22 billion by 2025. Statisticians project the data volume created by IoT connections to reach a massive total of 79.4 zettabytes by 2025. Combine this congenial condition with the flourishing Ransomware-as-a-Service (RaaS) business model – and what you get is possibly one of the most lethal cyber-attack vectors in the history of technology.
Now consider this – 75% of the respondents of a recent survey agreed on being highly reliant on cloud-based mobile apps; with 31% accepting of being lax on security restrictions when installing new mobile apps due to the ongoing pandemic. The survey also found that one in every 25 mobile apps has already leaked user credentials, at one point or another.
For those of you who are data-driven, the above-given numbers paint a rather gory picture of the device which has turned into an extension of your personality. And as such, mobile devices are fertile ground for disastrous ransomware attacks.
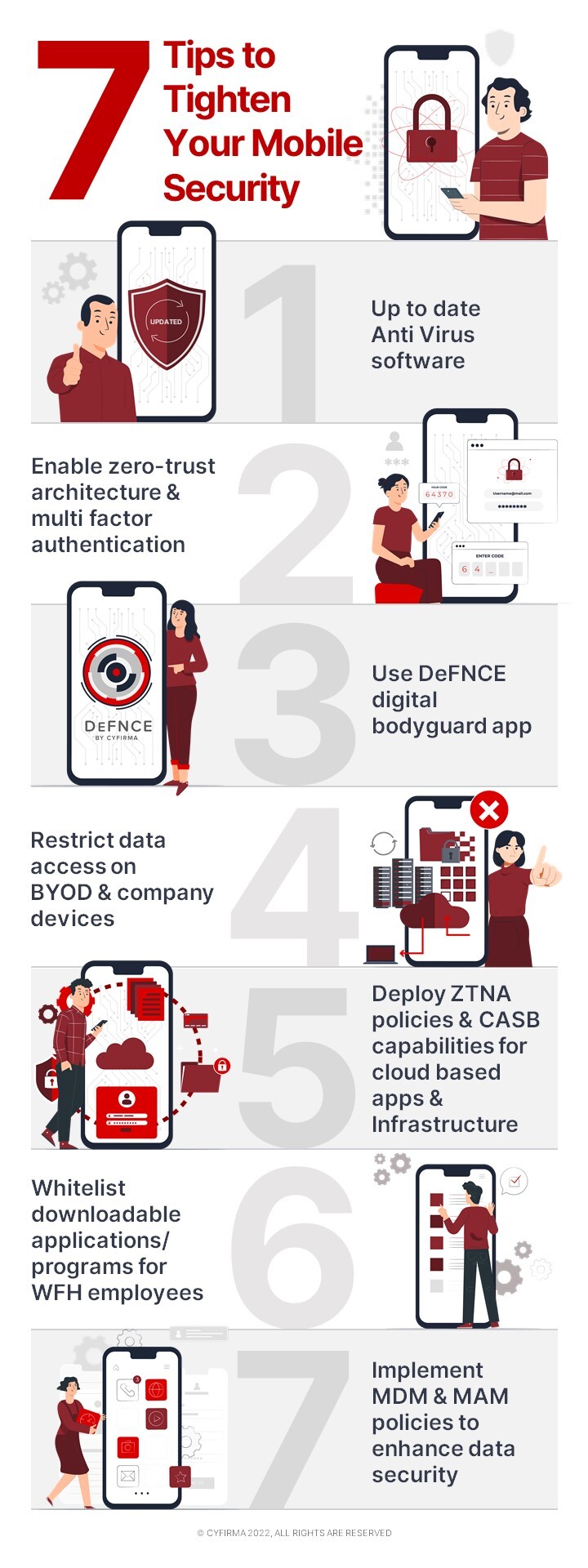
One of the best ways to boost up your mobile security is by keeping anti-virus software updated to detect and remove malicious software. Enabling zero-trust architecture and multi-factor authentication (MFA) to mitigate the compromise of credentials will go a long way in securing your mobile devices. Most of all, avoid installing mobile apps by clicking on links in emails, social media posts, text messages, and websites that look suspicious. Here at CYFIRMA, we recently released a mobile defence app that can help scan your device for possible data breaches and malicious apps.
This can be followed by restricting data access through the adoption of the principle of least privilege on both BYOD and company devices. Organizations can also ensure that only authorized and secure users or devices can access corporate infrastructure through zero-trust network access (ZTNA) policies for on-premises or private apps and cloud access security broker (CASB) capabilities for cloud-based apps and infrastructure.
Given that work from home (WFH) is the current norm, it will be prudent to direct traffic from mobile workers via special gateways with customized firewall and security controls such as content filtering and data loss prevention capability. Our cybersecurity experts also recommend restricting which applications may be installed through whitelisting (preferable) or blacklisting them.
Implementing Mobile Device Management (MDM) and Mobile Application Management (MAM) policies to enhance corporate data security providing monitoring, managing, and securing mobile devices such as laptops, smartphones, and tablets that are used in enterprises is another way in which organizations can beef up the security of mobile devices.
Lastly, as cliched as it can get, educating personnel about the security of their mobile device and social media security risks will be the best way to tackle ransomware attacks in the long term.